5 trends in Cybersecurity for 2024 and get ahead of technological threats
January 05, 2024
Table of contents
Quick Access
Threats and attacks on software products only get stronger and grow in number as the days go by, so companies and any individual with an application or website must focus on a robust cybersecurity system with what is necessary to block these attacks or be able to solve the damage they cause.
Cybersecurity refers to the practice of protecting computer systems, networks, and digital assets from unauthorized access, attacks, damage, or data theft. The main objective of cybersecurity is to guarantee the confidentiality, integrity and availability of information in the digital sphere. With the increasing dependence on digital technologies, the importance of cybersecurity has increased significantly to address changing threats in the cyber landscape.
By 2024, there are 5 clear trends in cybersecurity that we are going to explore in this article.
Cybersecurity trends for 2024
Artificial intelligence
It seems repetitive at this point, but the use of artificial intelligence will also be key in cybersecurity. It has several important uses in protecting users and software product data, including:
- Anomaly detection: AI algorithms analyze patterns of normal behavior in networks and systems. Deviations from these patterns, which may indicate potential threats, can be identified in real time.
- AI-powered antivirus: Traditional signature-based antivirus solutions are complemented by AI-powered antivirus programs that can identify and block new and unknown threats based on behavioral analysis.
- Endpoint Protection Platforms (EPP): AI-powered EPP solutions provide real-time protection against malware and other threats to endpoints by continually learning and adapting to new attack methods.
- Phishing Detection: AI algorithms can analyze email content, sender behavior, and other factors to detect and block phishing attempts, protecting organizations from email-based threats.
- Email Filtering: AI-based email filtering solutions can identify and filter malicious attachments, links and content, reducing the risk of malware infections.
By leveraging AI in these various ways, organizations can significantly improve their cybersecurity posture, staying one step ahead of cyber threats in an increasingly complex and dynamic digital landscape.
Internet of Things (IoT)
Integrating cybersecurity with Internet of Things (IoT) devices is crucial to ensure the security and privacy of connected systems. IoT devices, which include sensors, actuators, and other connected devices, present additional challenges due to their diverse nature and often limited computing resources. Implement end-to-end encryption for communication between IoT devices and backend systems. Encrypt sensitive data both in transit and at rest to prevent unauthorized access and tampering.
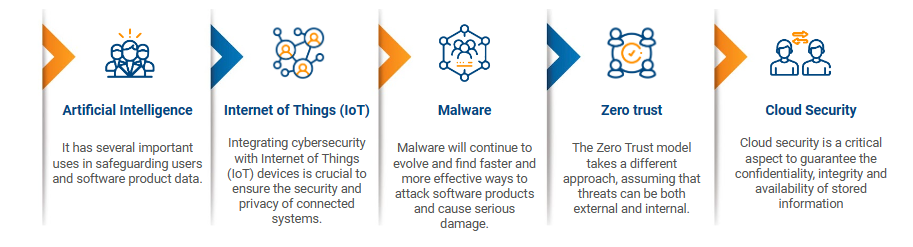
Malware
Malware will continue to evolve and find faster and more effective ways to attack software products and cause serious damage. Cybersecurity teams will focus on strengthening measures against these attacks, with techniques capable of detecting and stopping any malicious movement.
Zero trust
Zero Trust is a cybersecurity framework that assumes no trust, even within the corporate network. Traditional security models are often based on the concept of a trusted internal network and less secure external networks. However, in today's dynamic and evolving threat landscape, the Zero Trust model takes a different approach, assuming that threats can be both external and internal.
Cloud security
Cloud security refers to the set of policies, technologies and controls implemented to protect data, applications and infrastructure within cloud computing environments. Cloud security is a critical aspect to guarantee the confidentiality, integrity and availability of information stored and processed by cloud services.

As organizations increasingly adopt cloud computing for various purposes, including data storage, application hosting, and computing, the need to secure these cloud environments becomes paramount.
It must be remembered that the cybersecurity landscape is dynamic and new challenges and trends may emerge over time. Staying informed on the latest developments and continually updating security measures is crucial to maintaining a strong cybersecurity posture.
At Rootstack we have the team of security experts to strengthen your project against any attack. Do not hesitate to contact us to start working together.
We recommend you this video
Related Blogs

We were at MoveOn 2024! Rootstack sponsored one of the most important tech events in Panama
Vue.js or React for frontend development?


How to integrate UiPath RPA with a database