Top 5 Penetration Testing Tools
October 23, 2023
Table of contents
Quick Access
Penetration testing, often called ethical hacking, is a fundamental component of cybersecurity, a solution of great importance in any software product development to keep user data safe.
A penetration test involves simulating cyber attacks on a system, network, or application to identify vulnerabilities that malicious hackers could exploit. To conduct effective penetration testing, security professionals rely on a variety of tools and software designed to uncover weaknesses and strengthen the overall security posture.
In this article, we will explore the top five penetration testing tools that are widely used in the industry and with which any web or mobile application will have its weak points exposed.
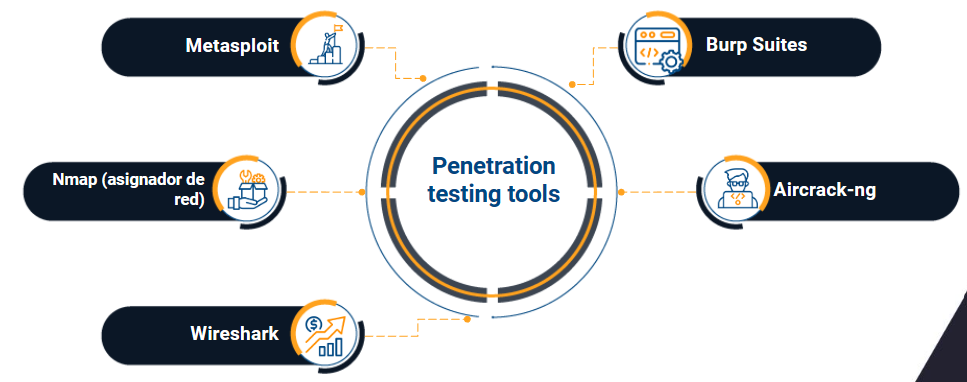
Penetration testing tools
1. Metasploit
Metasploit is one of the most popular and powerful penetration testing tools available. It provides a comprehensive framework for developing, testing, and executing exploits against a wide range of targets. Metasploit is known for its extensive database of exploits, payloads, and helper modules, making it an essential tool for both beginners and experienced penetration testers. The framework is also highly extensible, allowing users to create custom modules and scripts.
2. Nmap (network mapper)
Nmap, often called the "Swiss Army Knife" of network scanning, is an open source tool that helps discover hosts and services on a network. It excels at network mapping, port scanning and vulnerability detection. Nmap is particularly useful for collecting information about a target network, such as open ports, operating systems, and services running on multiple hosts. This information is invaluable to penetration testers in identifying potential attack vectors.
3. Wireshark
Wireshark is a popular network protocol analyzer that allows penetration testers to capture and inspect data on a network. It is particularly useful for identifying security problems, troubleshooting network problems, and analyzing network traffic. With Wireshark, testers can examine packets, decode protocols, and obtain information about communication between network hosts. It is an essential tool for monitoring and protecting network traffic.
4. Burp Suites
Burp Suite is a specialized tool for web application security testing. It offers a variety of features to scan, crawl, and attack web applications. Penetration testers use Burp Suite to discover vulnerabilities such as cross-site scripting (XSS), SQL injection, and insecure session management. It also helps automate tasks like scanning for vulnerabilities and identifying problems in web applications.
5. Aircrack-ng
Aircrack-ng is a set of tools specifically designed to evaluate and exploit Wi-Fi network security. It can be used to crack WEP and WPA/WPA2-PSK keys, making it valuable for testing the security of wireless networks. Aircrack-ng includes tools to capture packets, de-authenticate users, and perform dictionary attacks to crack Wi-Fi passwords. Penetration testers often rely on Aircrack-ng to evaluate the strength of wireless network security.
Importance of penetration testing tools and their proper use
Remember that penetration testing should always be performed responsibly and within the limits of the law and ethical guidelines. It is essential to obtain proper authorization and consent before testing any system, network or application.
These are just a few of the many penetration testing tools available. The choice of tools depends on the specific requirements of the test and the skills of the evaluator. To be an effective penetration tester, one must continually update their knowledge and skills to keep up with evolving cybersecurity threats and technologies.
Penetration testing tools are invaluable for identifying vulnerabilities and strengthening the security of systems and networks. The top five tools mentioned in this article are widely recognized and trusted within the cybersecurity community.
At Rootstack, within our cybersecurity services, we take penetration testing very seriously and thus verify that the software product will not be vulnerable to any attack from cyber hackers.
We recommend you on video
Related Blogs

Steps for software product development
-9.20.37-a.m.png)
Product Design and Development

Tools for Machine Learning

The Best Data Science Tools in 2025

What is Data Science?