
Cloud Security: Key Controls and Best Practices for Hybrid Cloud
Table of contents
Quick Access

You decided to migrate to the cloud. Your services are hosted in a virtual system where they can scale as needed and new data can be added without worrying about space. But is it secure? Cloud computing security is a topic that must be taken very seriously, which is why our experts created this article to discuss it.
As organizations evolve towards hybrid architectures that combine on-premises environments with public and private clouds, the risks and complexity of protecting data and systems also increase.
Hybrid cloud offers a powerful combination of flexibility, scalability, and control. However, to reap these benefits without compromising data integrity, companies must implement strong security controls, align with industry best practices, and often rely on cloud security firms with proven experience.
At Rootstack, with our ISO security certifications, we can offer your project the security guarantee necessary to ensure all cloud-hosted systems and data remain private, free from data leaks or malicious attacks.
Regarding hybrid cloud security, Red Hat noted: “Security is a top concern, regardless of where you are in your hybrid cloud journey, as 79% of companies consider it a challenge. Hybrid cloud security vulnerabilities are often due to the loss of control and oversight of resources, such as unauthorized use of the public cloud, lack of visibility, poor change control, poor configuration management, ineffective access controls, human error, and more. Unauthorized users can exploit these vulnerabilities to access sensitive data and internal resources, which can be costly.”

Key Security Controls to Protect Your Hybrid Cloud
Organizations need to go beyond traditional perimeter protection and adopt a multilayered approach, designed for the dynamic and distributed nature of hybrid cloud environments. Some of the cloud computing security controls you should keep on your radar include:
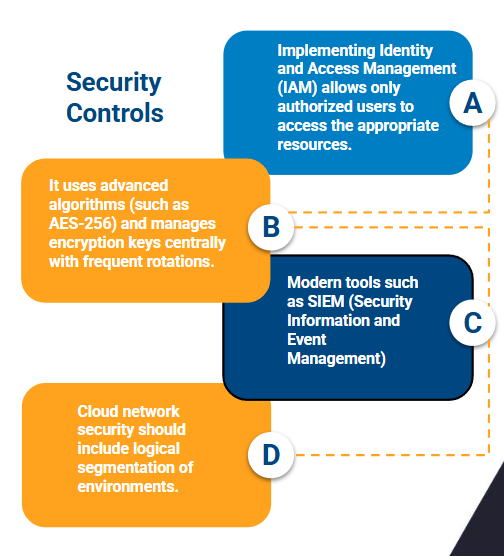
- Authentication and Access Control (IAM): A proper implementation of Identity and Access Management (IAM) ensures that only authorized users and services access the right resources at the right time. Applying the principle of least privilege and authenticating every access is essential, especially in distributed systems.
- Data Encryption in Transit and at Rest: Protecting sensitive information starts with a strong encryption policy. Use advanced algorithms (such as AES-256) and centrally manage encryption keys with frequent rotations to ensure data confidentiality and integrity.
- Continuous Monitoring and Threat Detection: Modern tools like SIEM (Security Information and Event Management) and XDR (Extended Detection and Response) solutions provide complete visibility across hybrid environments. They help detect unusual activity, vulnerabilities, and attacks in real time.
- Network Segmentation and Microsegmentation: Reducing the attack surface is critical. Cloud network security should include logical segmentation of environments, controlling traffic between applications and users with strict policies, even within the same cloud.
- Backups and Disaster Recovery: Resilience in the face of incidents depends not only on prevention but also on the ability to respond quickly. Design an automated backup plan with rapid restoration across multiple locations to ensure business continuity.
Best Practices for Hybrid Cloud Security
Beyond specific controls, adopting a strategic and adaptive approach will help you stay ahead of threats. Here are some of the best hybrid cloud security practices we recommend at Rootstack:
- Adopt a Zero Trust Mindset: The Zero Trust model assumes that no user or device should be trusted by default—not even within the corporate network. Everything must be continuously verified and authenticated. This is especially useful in hybrid environments where users work from various locations and devices.
- Implement Unified Compliance Policies: Regulations such as GDPR, HIPAA, and SOC 2 require strict controls over personal and sensitive data. Establish a consistent compliance policy for your entire hybrid ecosystem, centralizing management and auditing of your operations.
- Automate Security from Development: Integrate security throughout the DevOps cycle. Through the DevSecOps approach, you can automate vulnerability scans, security testing, and code reviews from the earliest phases, avoiding costly errors in production.
- Continuously Train Your Team: The human factor remains the weakest link. Provide ongoing training on phishing, good digital practices, and incident response protocols to reduce the risk of human error compromising security.
Related blogs

Banking software development company | Rootstack

Firewall solutions for IoT: Protect your business network

IoT Authentication: Key Methods for Protecting Devices

IoT penetration testing: Why it's crucial and necessary

Main IoT security risks and how to mitigate them
